Depeg Defense Mechanisms and Market Operations
This module explores the operational defenses that stablecoin issuers and protocol designers can implement to stabilize token value during stress events. It examines how redemption systems are structured, how liquidity support is coordinated with market makers, how automated circuit breakers operate on-chain, and how these elements converge into a responsive market operations framework.
What is a Depeg Defense?
Depeg Defense refers to mechanisms designed to protect a stablecoin from losing its peg (the fixed value it aims to maintain, usually 1:1 with the U.S. dollar). These mechanisms may include reserves, automatic trading strategies, or collateral management systems that act to restore the peg if the stablecoin’s price drifts away.
Redemption Mechanisms and User Incentives
At the core of peg stability lies the redemption process. A stablecoin is considered trustworthy if users can redeem it on demand for its equivalent fiat or backing asset at par value. Redemption systems serve as both psychological and economic anchors, reinforcing user belief in the value of the token. However, the mechanics of redemption are complex and can vary significantly depending on the issuer’s structure and the stablecoin’s collateralization model.
In fiat-backed models, redemption typically involves a centralized entity receiving stablecoins from users and delivering the corresponding fiat through bank transfers or payment processors. Redemption may be offered only to whitelisted or institutional users, with minimum thresholds or fees applied. The latency of fiat settlement and potential bottlenecks in banking rails mean that redemption systems must be designed for both scalability and fairness. In moments of stress, demand for redemptions can spike dramatically, and systems must be able to queue, prioritize, or batch redemptions to maintain orderly processing.
Some issuers implement priority queues based on redemption size, account verification status, or the timing of requests. Others adopt pro-rata models, where redemption requests are partially filled during constrained liquidity conditions. While these controls aim to preserve system integrity, they may also weaken user confidence if perceived as arbitrary or opaque. Therefore, transparency in redemption rules is essential, especially during periods of market uncertainty.
For crypto-collateralized models, redemption may involve repaying a debt position or triggering liquidation mechanisms that exchange the stablecoin for collateral. These processes are governed by smart contracts and are subject to collateral valuation rules, oracle accuracy, and transaction fees. In some cases, users may choose to hold rather than redeem, relying on arbitrage mechanisms to realign the peg through trading activity rather than formal redemption. Regardless of the design, the ability to redeem at or near par value in real terms is fundamental to peg defense.
Market Maker Programs and Liquidity Provisioning
Stablecoin stability also depends on the availability of deep and responsive liquidity in secondary markets. During times of imbalance, traders must be incentivized to buy the stablecoin when it trades below peg and sell when it trades above. Market makers play a central role in facilitating this equilibrium by providing continuous bid-ask quotes, absorbing supply-demand shocks, and narrowing spreads across venues.
To encourage participation and reliability, issuers often establish formal market maker programs. These arrangements may involve financial incentives such as rebates, fee reductions, or direct liquidity support. In some cases, market makers are granted preferential access to primary issuance or redemption channels, enabling them to arbitrage peg deviations more efficiently. Program terms typically include quoting obligations, minimum depth requirements, and performance monitoring.
Effective liquidity provisioning requires coordination across multiple trading venues, including centralized exchanges, decentralized exchanges (DEXs), and over-the-counter (OTC) networks. Market makers must deploy capital efficiently and move inventory dynamically across platforms to ensure that stablecoin pricing remains aligned globally. Issuers may assist by providing on-chain liquidity incentives through mechanisms such as liquidity mining, where token rewards are allocated to participants who supply stablecoin pairs in automated market makers.
Cross-market arbitrage further reinforces peg stability. When a stablecoin trades below its peg on one exchange and above on another, arbitrageurs purchase on the discount market and sell on the premium market, thereby equalizing prices. These dynamics require low latency execution, transparent pricing, and sufficient bridge liquidity between venues. Disruptions in any of these components, such as delayed settlement, transaction congestion, or impaired bridge access, can impair the effectiveness of arbitrage and delay peg recovery.
Automated Protocol Safeguards and Circuit Breakers
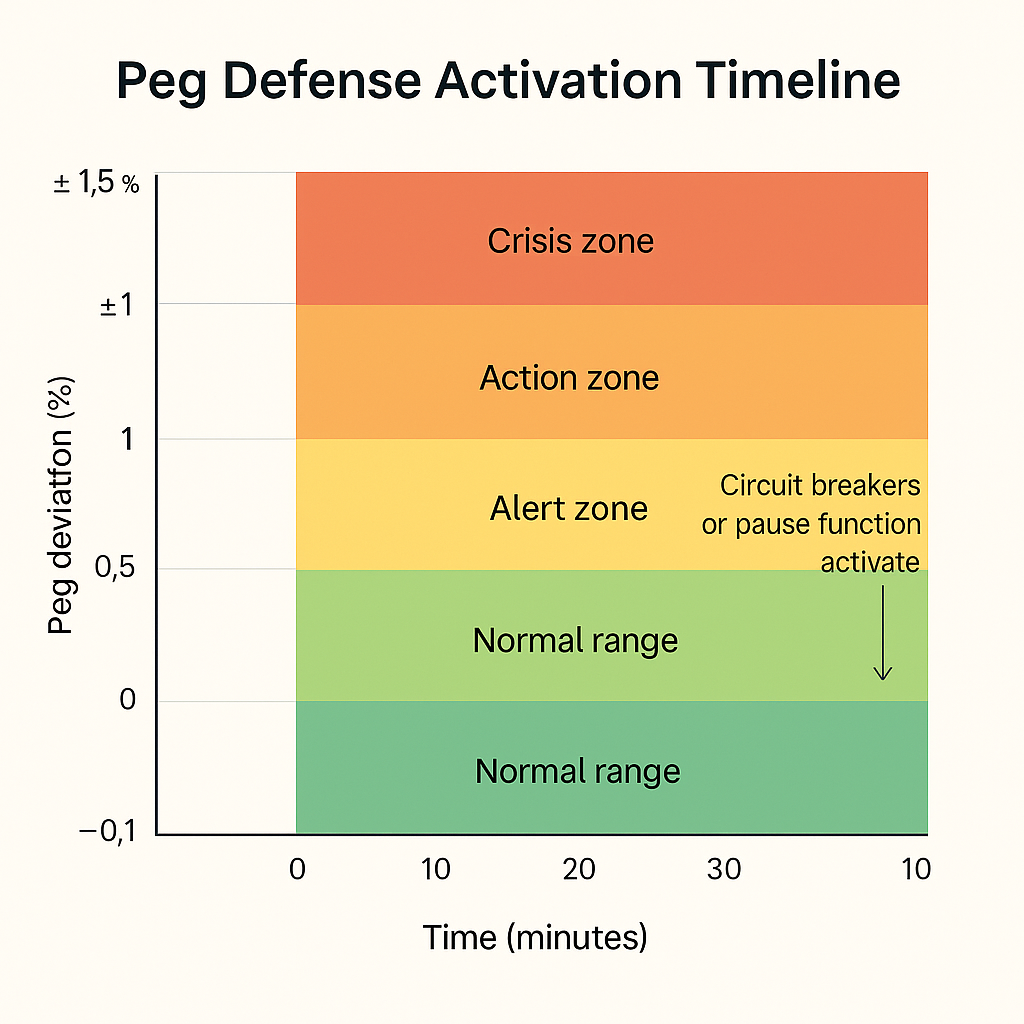
Beyond manual operations and external incentives, many stablecoins incorporate automated defense mechanisms directly into protocol design. These mechanisms act as circuit breakers, pausing minting or redemption functions, freezing liquidity operations, or imposing constraints on token flows during abnormal conditions. Their purpose is to prevent self-reinforcing feedback loops, protect reserves, and provide time for coordinated intervention.
Circuit breakers are typically triggered by predefined thresholds, such as a sustained deviation from peg, excessive minting volume, or abnormal volatility in collateral assets. When activated, they may halt minting of new stablecoins to prevent dilution or pause redemptions to conserve liquidity. In more sophisticated systems, circuit breakers can reallocate liquidity, shift reserve composition, or impose temporary caps on trading pairs. These actions are designed to slow down system interactions during crises and reduce the probability of cascading failure.
The governance of circuit breakers is a critical design choice. In some models, they are fully automated and triggered by smart contracts without human discretion. In others, they require approval by a multisignature governance committee or a decentralized autonomous organization (DAO). The trade-off lies between speed and flexibility. Automated systems respond instantly but may lack situational judgment, while human intervention introduces latency but can incorporate external context.
Transparency is essential in the operation of circuit breakers. Users must understand the conditions under which they may be unable to redeem or transfer stablecoins and what criteria will be used to restore normal operations. Poorly communicated restrictions may trigger panic rather than confidence. Therefore, protocol designers must publish clear documentation, status indicators, and recovery plans as part of their public defense architecture.
Managing Multi-Venue and Cross-Chain Liquidity
As stablecoins increasingly operate across multiple blockchains and trading venues, peg defense must account for the complexity of fragmented liquidity. A stablecoin may be issued natively on one chain and bridged to others through third-party protocols. Each environment may have different levels of liquidity, oracle coverage, and infrastructure reliability. In such cases, price deviations on one venue or chain can spill over into others, creating inconsistent valuations and undermining confidence.
Liquidity fragmentation makes defense coordination more difficult. A depeg event may originate in a low-liquidity venue and propagate through bridge mechanisms to affect global pricing. Stablecoin issuers must monitor liquidity flows across chains and deploy assets accordingly. This often requires maintaining cross-chain liquidity buffers, participating in bridge design governance, and integrating multi-chain oracles. It also means establishing partnerships with market makers who can operate in cross-chain environments and respond to arbitrage opportunities at speed.
Some issuers manage this complexity by deploying native stablecoin versions on each supported chain, each backed by a centralized reserve and synchronized through controlled issuance. Others rely on wrapped tokens or synthetic assets that mirror the primary token but are collateralized differently. Each method introduces specific risks in terms of custody, bridge reliability, and depegging exposure. The choice of architecture should be aligned with the issuer’s risk tolerance and operational capacity to manage cross-chain defense mechanisms.
In any multi-venue environment, communication and execution speed are essential. Defense strategies must account for differences in transaction finality, bridge latency, and trading infrastructure across chains. Incident response coordination must also be rehearsed and documented in advance to prevent fragmented responses during stress events. As stablecoins continue to expand their cross-chain footprint, liquidity coherence becomes a first-order concern in maintaining a global peg.
Simulating Peg Instability and Response Execution
To evaluate the readiness of depeg defense mechanisms, stablecoin teams must regularly conduct simulations of crisis scenarios. These exercises model the sequence of events during a peg deviation and test the activation, coordination, and performance of defense tools under time pressure. A typical simulation may begin with a price deviation caused by market sell-offs or reserve valuation shock, followed by liquidity drain across trading venues and a spike in redemption requests.
The simulation tests whether monitoring systems detect the deviation promptly, whether alerts are escalated properly, and whether circuit breakers or redemption controls engage as expected. It evaluates the ability of market makers to respond to arbitrage opportunities and the capacity of treasury operations to rebalance liquidity. Governance actors may also be involved to simulate approval flows for discretionary interventions such as capital injection or protocol parameter changes.
Simulations reveal not only technical weaknesses but also procedural delays, coordination gaps, and communication failures. In mature systems, these insights are captured in post-mortem documentation and used to refine operational protocols. Some regulators now view simulation exercises as part of a stablecoin issuer’s duty to demonstrate resilience and preparedness. At scale, a failed simulation may point to deeper architectural fragility that requires fundamental redesign.
Simulation frameworks should include defined metrics for success, such as time to peg recovery, redemption backlog clearance, or market spread normalization. They should be repeated periodically and adjusted for changes in market structure, reserve composition, or protocol rules. Ultimately, the value of a defense mechanism lies not in its theoretical design but in its proven ability to stabilize the peg under real or simulated pressure.





